topics of the tutorials
DoS (Denial of Service) Attack
Best Penetration Testing (Pen Testing) Tools
13 BEST Operating System for Hacking
11 Best Wireshark Alternatives
13 BEST Vulnerability for Websites, Network
17 Best IP & Network Scanning Tools
What is Social Engineering?
Social engineering is the art of manipulating users of a computing system into revealing confidential information that can be used to gain unauthorized access to a computer system. The term can also include activities such as exploiting human kindness, greed, and curiosity to gain access to restricted access buildings or getting the users to installing backdoor software.
Knowing the tricks used by hackers to trick users into releasing vital login information among others is fundamental in protecting computer systems
In this tutorial, we will introduce you to the common social engineering techniques and how you can come up with security measures to counter them.
How social engineering Works?
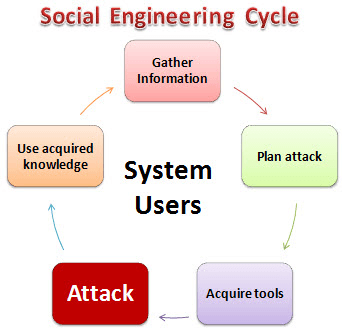
HERE,
- Gather Information: This is the first stage, the learns as much as he can about the intended victim. The information is gathered from company websites, other publications and sometimes by talking to the users of the target system.
- Plan Attack: The attackers outline how he/she intends to execute the attack
- Acquire Tools: These include computer programs that an attacker will use when launching the attack.
- Attack: Exploit the weaknesses in the target system.
- Use acquired knowledge: Information gathered during the social engineering tactics such as pet names, birthdates of the organization founders, etc. is used in attacks such as password guessing.
Common Social Engineering Techniques:
Social engineering techniques can take many forms. The following is the list of the commonly used techniques.
- Familiarity Exploit: Users are less suspicious of people they are familiar with. An attacker can familiarize him/herself with the users of the target system prior to the social engineering attack. The attacker may interact with users during meals, when users are smoking he may join, on social events, etc. This makes the attacker familiar to the users. Let’s suppose that the user works in a building that requires an access code or card to gain access; the attacker may follow the users as they enter such places. The users are most like to hold the door open for the attacker to go in as they are familiar with them. The attacker can also ask for answers to questions such as where you met your spouse, the name of your high school math teacher, etc. The users are most likely to reveal answers as they trust the familiar face. This information could be used to hack email accounts and other accounts that ask similar questions if one forgets their password.
- Intimidating Circumstances: People tend to avoid people who intimidate others around them. Using this technique, the attacker may pretend to have a heated argument on the phone or with an accomplice in the scheme. The attacker may then ask users for information which would be used to compromise the security of the users’ system. The users are most likely give the correct answers just to avoid having a confrontation with the attacker. This technique can also be used to avoid been checked at a security check point.
- Phishing: This technique uses trickery and deceit to obtain private data from users. The social engineer may try to impersonate a genuine website such as Yahoo and then ask the unsuspecting user to confirm their account name and password. This technique could also be used to get credit card information or any other valuable personal data.
- Tailgating: This technique involves following users behind as they enter restricted areas. As a human courtesy, the user is most likely to let the social engineer inside the restricted area.
- Exploiting human curiosity: Using this technique, the social engineer may deliberately drop a virus infected flash disk in an area where the users can easily pick it up. The user will most likely plug the flash disk into the computer. The flash disk may auto run the virus, or the user may be tempted to open a file with a name such as Employees Revaluation Report 2013.docx which may actually be an infected file.
- Exploiting human greed: Using this technique, the social engineer may lure the user with promises of making a lot of money online by filling in a form and confirm their details using credit card details, etc.
Social Engineering Counter Measures
Most techniques employed by social engineers involve manipulating human biases. To counter such techniques, an organization can;
- To counter the familiarity exploit, the users must be trained to not substitute familiarity with security measures. Even the people that they are familiar with must prove that they have the authorization to access certain areas and information.
- To counter intimidating circumstances attacks, users must be trained to identify social engineering techniques that fish for sensitive information and politely say no.
- To counter phishing techniques, most sites such as Yahoo use secure connections to encrypt data and prove that they are who they claim to be. Checking the URL may help you spot fake sites. Avoid responding to emails that request you to provide personal information.
- To counter tailgating attacks, users must be trained not to let others use their security clearance to gain access to restricted areas. Each user must use their own access clearance.
- To counter human curiosity, it’s better to submit picked up flash disks to system administrators who should scan them for viruses or other infection preferably on an isolated machine.
- To counter techniques that exploit human greed, employees must be trained on the dangers of falling for such scams.














